LawToolBox Apps for Office 365, Delegated Permissions, and Application Permission
LawToolBox leverages delegated permissions (and for some enterprise clients that opt in an application permission) to control users access to create, read, edit and delete data on the end-user’s tenant. LawToolBox intentionally and purposefully limits the amount of client data that we store on our server’s, instead opting to function as a dashboard to the client’s data stored on their own tenant and safely locked behind the Microsoft 365 secure network, and which can only be unlocked with the end-users own Office 365 credentials.
A. User Credentials Are Required to Unlock Tenant Information.
The LawToolBox integration with office 365 has been designed to leverage the security features of the hardened security platform that Microsoft spends $1 billion a year protecting.
By relying on delegated permissions LawToolBox outsources to Microsoft the enforcement of the access rights an organization has already granted a user. We store the minimum level of information on the end-user organization, users and matters to serve as a dashboard to enhance and amplify Microsoft 365 with unique functions.
Because the data stored within the end-user’s Microsoft tenant can only be unlocked with a specific users Office 365 user name and password, the end-users data is safely stored behind Microsoft’s steel curtain, and LawToolBox never has access or visibility to this information.
Our goal is the secure and safe pursuit of making collaboration and the management of information as easy and powerful as we can.
B. What end-user matter data does LawToolBox store?
LawToolBox stores the end-user’s Tenant ID, matter names, group ID, group name, user names, UPN, User Object AAD ID, OneNote ID, and any matter calendar event created through LawToolBox. The SSO authentication allows the end-user to use LawToolBox apps to access data in their tenant that the end-user already has access to through their own instance of Office 365.
Importantly, at no point does LawToolBox have access to end-user’s data stored on their Office 365 tenant. In other words, granting permission for the LawToolBox app to “Sign you in and read your profile” doesn’t give LawToolBox access to any of this information, it instead allows the end-user to use this permission to “sign in” and “read their own profile” inside the LawToolBox app.
Other than information necessary to point the end-user to data and information on their tenant, LawToolBox does store matter names, basic matter reference information, calendar events descriptions, and contact information on our servers.
C. End-user Data from the user’s Office 365 Tenant is Not Stored on any LawToolBox servers.
. LawToolBox does not pull any data when users are not online, and LawToolBox only stores a masked reference to the end-user files or emails.
For example, when an end-users saves an email using LawToolBox, the content of the email is never stored on a LawToolBox server at any stage of the life of that email (in contrast other products will save the confidential email onto their servers and then convert it to a pdf file before enabling storage in a folder).
After an email is saved, LawToolBox uses delegated permission to retrieve the list of emails and files through Microsoft Graph API, which we then display inside LawToolBox. We retrieve (but do not store) the URL of the email, the creation date of the email, and the subject of each email we display.
If the user clicks on the URL the can access the email within the Microsoft security framework for delegated permissions.
D. LawToolBox Permissions.
All the permissions listed below operate under the user delegated scope. All the permissions are documented in the below Microsoft document: https://docs.microsoft.com/en-us/graph/permissions-reference
1. Have full access to your calendars – this permission is restricted accessing the user’s access to calendars that they already have access to – we use this to allow users to retrieve their own calendar information. The end-user only has access to retrieve their own calendar information inside LawToolBox (the same information they could retrieve by opening their Outlook calendar). The end-user is not granted additional permission to open anyone else’s calendar. LawToolBox does not have access to any information retrieved from use of this permission.
2. Have full access of your contacts – this permission is restricted accessing the user’s contacts that they already have access to. We use this permission to allow user to search their O365 contacts and add to LawToolBox – we do not automatically add any contact (this can be revoked if you do not want this feature and contacts can be manually added).
3. Read and write to your and shared contacts – we use this permission to allow user to search shared O365 contacts and add to LawToolBox – we do not add any contacts automatically.
4. Read and write directory data – we use in admin portal to retrieve list of users from O365 tenant to add to LawToolBox. This permission operated under delegated permission and is REQUIRED TO MANAGE GROUPS.
The end-user only has the same ability to read and write directory data that they have access to natively inside Office 365. This permission does not grant extra rights to the end-user, and this permission does not enable LawToolBox to access this information.
5. Have full access to your files – we read files from Teams, Groups and OneDrive for meetings (if you revoke it will prevent LTB from listing matter files in our apps
In March 2021 LawToolBox plans to changed/degrade this permission to READ ONLY.
The end-user only has the same ability to access files that they have access to natively inside Office 365. This permission does not grant extra rights to the end-user, and this permission does not enable LawToolBox to access this information (instead it allows LawToolBox to create a tunnel where the end-user can use their own credentials through SSO to manage Office 365 using Microsoft Graph API).
6. Read and write all groups – this is necessary to read the Teams API, create Teams, create Calendar event, create channels, Teams file sharing feature. REQUIRED TO MANAGE GROUPS.
The end-user only has the same ability to read and write to groups that they have access to natively inside Office 365. This permission does not grant extra rights to the end-user, and this permission does not enable LawToolBox to access this information (instead it allows LawToolBox to create a tunnel where the end-user can use their own credentials through SSO to manage Office 365 using Microsoft Graph API).
7. Read your mail – we use this permission to read PACER emails in our outlook add-in to auto open that matter and also to read contacts from your email to add to our contact system
8. Send mail as you – LawToolBox uses this sending emails as the user to develop a function to.
In February 2021 LawToolBox plans to remove this permission entirely.
9. Read and write all OneNote notebooks that you can access – users can write any notes to OneNote
10. Read and create your online meetings – necessary to create meetings
11. Read your relevant people list – used to suggest recent contacts to add to meetings or contacts
12. Sign you in and read your profile – necessary for SSO authentication (we don’t ask for permission to write to your profile) THIS PERMISSION IS REQUIRED FOR USERS TO SIGN INTO LAWTOOLBOX APPS USING SINGLE SIGN ON AUTHORIZATION.
13. Read and write items and lists in all site collections– related to reading files and creating case folders and files– so files can be uploaded to SharePoint for a specific matter – this facilities SharePoint search (virtual meeting uses this function) (required for “Copy Template” functionality) (delegated permission only)
14. Read items in all site collections – related to files and folders for uploading files to case folders and file sharing in meetings– so files can be uploaded to SharePoint for a specific matter – this facilities SharePoint search (virtual meeting uses this function)
15. Read your files – read and list the user files the user already has access to
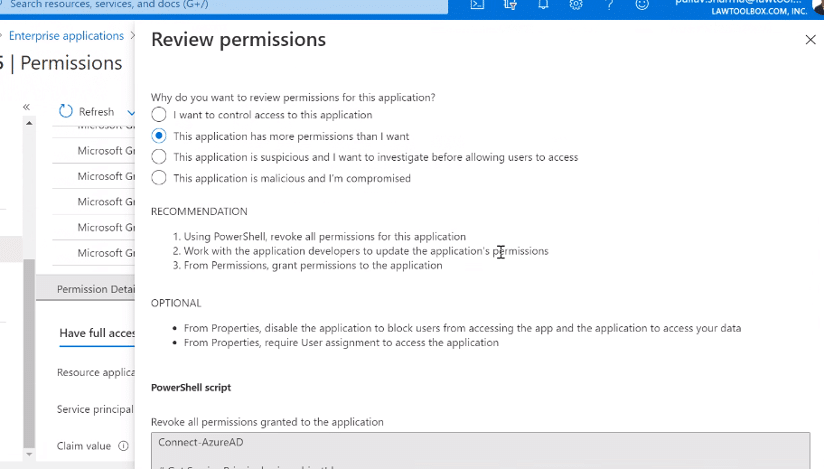
E. Revoking Individual Permissions.
If certain permissions are revoked, it will deprecate functions of LawToolBox. From your Azure portal the global admin can run a PowerShell command to revoke specific permissions in our apps. See, PowerShell for Delegated Access Permissions.
F. APPLICATION PERMISSION.
For enterprise organizations, if “application permission” is granted, this is outside of delegated permission structure, and it allows an end-user to create more than 250 groups, and to add and remove users from groups that user is not a member of.
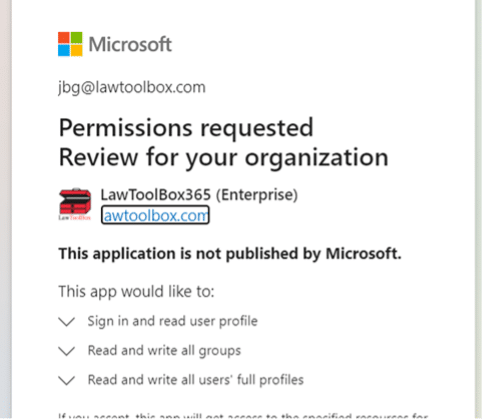
The LawToolBox apps for Office 365 can function without this application permission being granted, but this permission makes it easier for a designated LawToolBox admin to share and unshare cases.